Phishing Definition
Phishing is a form of cybercrime that aims to deceive individuals into providing sensitive information, such as usernames, passwords, credit card details, and other personal data. It typically occurs through fraudulent communications, often appearing to be from legitimate sources, such as banks, email providers, or online services. As technology evolves, so do the tactics used by cybercriminals, making it increasingly important for individuals and organisations to understand how these attacks work and how to protect themselves against it.
How Phishing attacks work
Attacks often start with a seemingly innocuous email or message. Detection can be challenging. These communications can be meticulously crafted to look like they come from trusted sources. For example, an attacker might create a fake email that mimics a bank’s communication, urging the recipient to verify their account information. The message usually includes a link that leads to a fraudulent website designed to collect the victim’s credentials.
The common elements of a Phishing attempt include:
- Urgency: Many of these messages create a sense of urgency, prompting recipients to act quickly. Phrases like “Your account will be suspended unless you act now!” are typical.
- Generic Greetings: These messages often use generic salutations like “Dear Customer” instead of personalizing the greeting. This is a telltale sign of a scam. Sometimes you can tell this sort of email apart from legitimate emails because you see no recipients and you are added in as a BCC.
- Suspicious Links: Links in an email may appear legitimate but lead to malicious websites. Hovering over a link can reveal the true URL, often indicating a different domain than the purported sender. Sometimes URL shortening or Unicode is used to disguise the link, making it more difficult to separate from an innocent link.
- Attachments: One attack style includes malicious attachments that, when opened, can install malware on the victim’s device. This is usually paired with an email claiming to be an invoice or a recording.
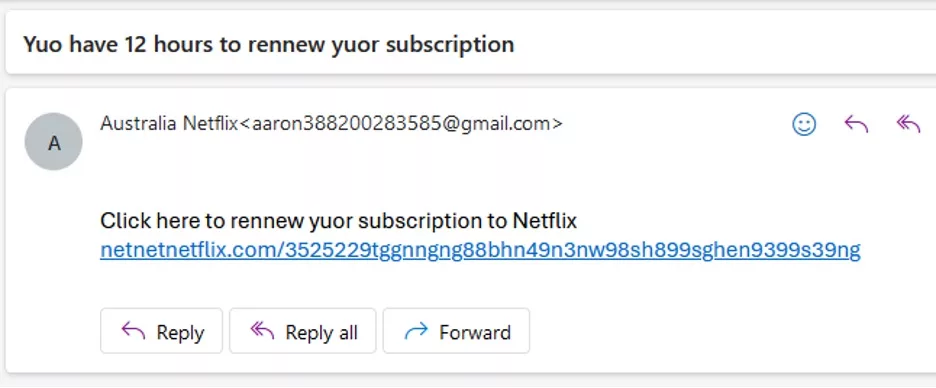
Below is an example of a phishing email, see if you can spot what makes this email different from a legitimate email.
Types of Phishing Cybersecurity Attacks
An attack can take many forms. Each style of attack has its unique methods and targets. Here are some common forms:
- Phishing: The most prevalent form, where attackers send mass emails to numerous recipients with the expectation that most emails will fail. Often done automatically by bots or by first timers just getting into cybercrime.
- Spear Phishing: This targeted approach focuses on specific individuals or organizations. Attackers gather personal information to craft personalised messages that are more convincing.
- Whaling: A form of spear phishing aimed at high-profile targets, such as executives or key decision-makers within a company.
- Voice Phishing (Vishing): Attackers use phone calls to deceive victims into revealing personal information, often impersonating legitimate entities.
- SMS Phishing (Smishing): Similar to voice, but conducted through text messages. Attackers send texts that prompt users to click on malicious links.
- Clone Phishing: In this method, a legitimate email previously sent is duplicated, and the original link is replaced with a malicious one. The attacker may claim that the email was resent due to an issue.
- Business Email Compromise (BEC): This sophisticated scam targets businesses, where attackers impersonate a company executive to trick employees into transferring funds or divulging sensitive information.
Impact of Attacks
The consequences of attacks can be severe and undermine both information security and cybersecurity. Even the simplest phishing attacks could have devastating consequences, which could involve the loss of millions of dollars, the identity theft of your employees and clients and the leak of your intellectual property. More sophisticated attacks would add persistent malware to your business devices allowing the cybercriminal to siphon money and information from your device until it is stopped, assuming it could be found.
Phishing Statistics and Examples
These attacks continue to be a major cybersecurity threat in 2024, with email remaining the most prevalent form. According to SlashNext’s 2024 Phishing Intelligence Report, there was a staggering 202% increase in overall scam messages in the second half of 2024, accompanied by a 703% surge in credential-based attacks.
The Anti-Phishing Working Group (APWG) reported that in the third quarter of 2024, they have detected over 932,000 unique phishing attacks. These attacks were becoming increasingly personalized, even taking Google Street View images of the victim’s homes. This alarming trend is further emphasised by GreatHorn’s findings that 57% of organisations face scam attempts weekly or daily.
While email attacks remain dominant, other forms are gaining traction. Voice attacks have increased by 30% in the last year, with 70% of organizations unknowingly sharing sensitive information during voice simulations. Smishing (SMS) is also on the rise, with Americans receiving an average of 41 spam texts per person each month. Business Email Compromise (BEC) continues to be a significant threat, with the FBI identifying $51 billion in exposed losses due to BEC.
Whaling attacks, targeting high-profile executives, have also seen an uptick, with one high-performance networking technology business losing $39 million in a single incident. The financial impact of attacks is substantial. Businesses lose an estimated $17,700 every minute due to attacks. The average cost of a data breach in the U.S. was $9.48 million, with phishing being a significant contributor. BEC attacks, while only accounting for 4% of breaches, have an average cost of $5.01 million per breach to businesses.
These statistics underscore the critical need for organisations to implement robust cybersecurity measures and provide comprehensive training to employees. The rise of AI-powered attacks, which are becoming increasingly difficult to detect, further emphasizes the importance of staying vigilant and adapting security strategies to combat evolving threats.
Recognizing a Phishing Scam
Awareness is the first line of defense against an attack. Here are some key indicators to help recognise attempts:
- Check the Sender’s Email Address: Look closely at the sender’s address. Scam emails often come from addresses that are similar to, but not exactly, the legitimate domain. While it is possible to spoof the email address, it is really uncommon for that technique to be used.
- Beware of Poor Grammar and Spelling: Many scam messages contain grammatical errors or awkward phrasing, which can be a red flag.
- Look for Unusual Requests: Legitimate organizations rarely ask for sensitive information through email. Be suspicious of any message requesting such data.
- Verify Links Before Clicking: Always hover over links to see where they lead before clicking. If unsure, visit the website directly by typing the URL into your browser. Even better would be to bookmark URLs, cybercriminals like to squat on lookalike URLs just in case someone accidentally mistypes a URL.
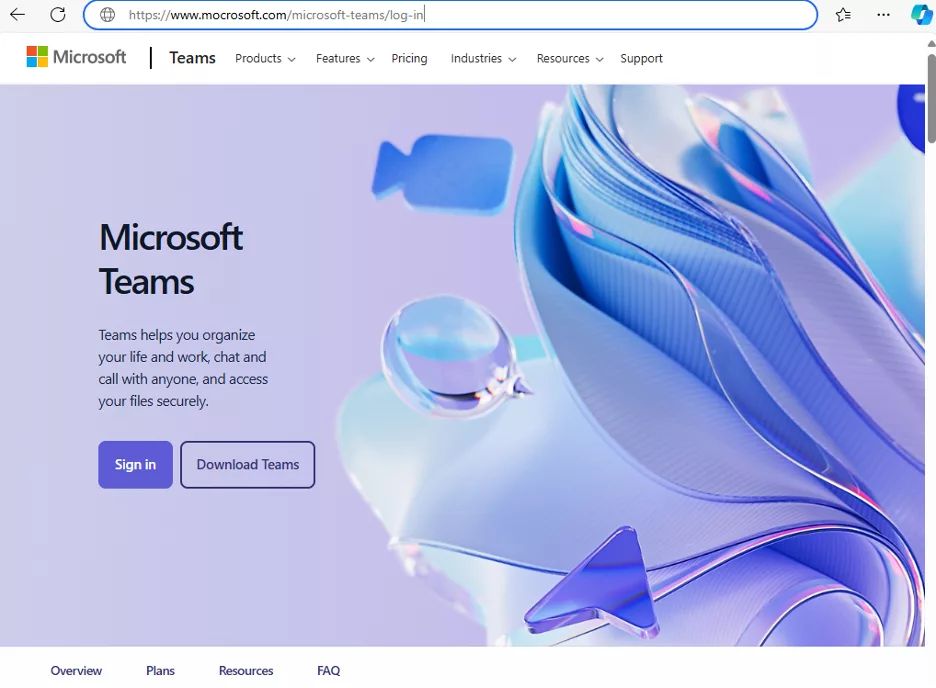
You’re in a hurry because you’re about to be late to a teams meeting. Can you spot what is wrong with this teams log in page?
Preventive Cybersecurity Measures Against Phishing
Preventing attacks requires a combination of technological solutions, education, and best practices:
- Employee Training: Organizations should regularly educate employees about tactics, encouraging them to recognize and report suspicious messages. Employees will either be the weakest link or the most important part of defending your organization from cyber security threats making training the most important step out of all of these steps.
- Email Filtering: Implementing robust email filtering systems can help detect and block attempts before they reach users’ inboxes. Unfortunately even the best email filters will miss new scams, of which many are invented every day.
- Incident Response Plans: Organizations should have clear procedures for responding to suspected incidents, including reporting protocols and damage control strategies.
- Raising Awareness: You can raise awareness to your coworkers and family, show them this site so they too can know how to identify an attack before it does any damage.
- Use Multi-Factor Authentication (MFA): Enabling MFA adds an extra layer of computer security, making it more difficult for attackers to gain access even if they obtain your password. Just watch out for attacks aimed at getting your MFA, this form of attack is becoming more common as more and more people start using MFA.
Conclusion
Phishing remains one of the most common and effective cyber threats today. Understanding its mechanics, recognising its signs, and implementing prevention measures can significantly reduce the risk of falling victim to these attacks. As cybercriminals continue to refine their techniques, ongoing cybersecurity training, education and vigilance are essential for both individuals and organizations. By staying informed and proactive, we can build a safer digital environment for everyone.
How we can help you
One of our services is a cheap and effective training program designed to teach you and others around you how to identify phishing, smishing and other related internet related scams such as romance scams.
Are you a business/NGO seeking to protect you and your organization from these scames? Our cybersecurity training program might be perfect for you. You can leverage our expertise in areas that include information security, network security and endpoint security. Just sign up below to try it out.
QUESTIONS AND ANSWERS
Q: What are some common methods used in Phishing emails?
A: Scam emails often employ various tactics to appear legitimate, including:
- Spoofing sender addresses to mimic trusted sources
- Using urgent or threatening language to prompt immediate action
- Including malicious links or attachments
- Requesting sensitive information under false pretences
- Mimicking the design and layout of legitimate companies
Recognizing these steps is crucial for improving your cybersecurity protection and warding off attacks.
Q: What steps can I take to protect myself from Phishing attacks?
A: To protect yourself from attacks, follow these cybersecurity recommendations:
- Be cautious of unsolicited emails, especially those requesting personal information
- Verify the sender’s email address and look for signs of spoofing
- Hover over links before clicking to check their true destination
- Use strong, unique passwords for each account
- Enable two-factor authentication when available
- Keep your software and operating systems up-to-date
- Use reputable antivirus software and email security
- Educate yourself on the latest cybersecurity threats
Q: How can organizations implement effective prevention strategies?
A: Organizations can implement several strategies to prevent attacks:
- Conduct regular security awareness training for employees
- Implement email filtering and anti-spam solutions
- Use DMARC, SPF, and DKIM protocols to authenticate emails
- Establish clear policies for handling sensitive information
- Regularly test employees with simulated campaigns
- Implement multi-factor authentication across all systems
- Keep all software and systems updated with the latest security patches
- Use endpoint security to protect individual devices
These measures can significantly improve an organisation’s overall cybersecurity preparation.
Q: What role does cyber security training play in prevention?
A: Cyber security training is crucial as it:
- Raises awareness about the latest cybersecurity threats and tactics
- Teaches employees to recognize and report suspicious emails
- Provides hands-on experience through simulated attack exercises
- Educates staff on handling sensitive information
- Keeps the workforce informed about the organization’s security policies 6. Helps create a culture of cyber safety within the organization
Regular training is essential for maintaining strong information security and reducing the risk of successful attacks.
Q: How can I recover if I’ve fallen victim to a phishing attack?
A: If you’ve fallen victim to an attack, take these steps:
- Immediately change passwords for all affected accounts
- Contact your bank or credit card company if financial information was compromised
- Run a full scan with up-to-date antivirus software
- Monitor your accounts for any suspicious activity
- Report the incident to your IT department or relevant authorities
- Consider freezing your credit to prevent identity theft
- Be cautious of potential follow-up attacks or scams
Quick action and thorough recovery steps can help minimise the damage from an attack.
Q: What are some recommended cybersecurity resources for staying informed about this threat?
A: To stay informed about the latest threats and cybersecurity best practices, consider these resources:
- National Cyber Security Centre (NCSC) website and alerts
- US Cybersecurity and Infrastructure Security Agency (CISA) publications
- NIST Cybersecurity Framework
- Australian Cyber Security Centre advisories
- Australian Signals Directorate
Regularly consulting these resources can help you stay up-to-date with the evolving threat landscape and improve your overall cybersecurity posture.
Q: How can businesses assess their vulnerability to attacks?
A: Businesses can assess their vulnerability to attacks through:
- Conducting regular security audits
- Performing penetration testing and vulnerability scans
- Implementing simulated attack campaigns
- Analysing employee response rates to security awareness training
- Reviewing incident response plans and procedures
- Assessing the effectiveness of current security solutions
Consulting with cybersecurity experts for a comprehensive evaluation Regular assessments help identify weaknesses in an organisation’s cybersecurity defences and guide improvements in prevention strategies.